As a Human Resources (HR) professional you are involved in the most private aspects of your fellow employees’ work lives. You’re an expert in compensation and benefits, managing numerous uncomfortable topics, such as substance abuse, workplace hostility and unethical behaviour.
You also know that employee data privacy is core to the employee experience and employee retention, but the digital transformation of human resources to electronic data storage has made protecting employee privacy a lot more complicated. Digital records make life much easier for HR professionals…but they also make sensitive data much easier to steal.
Compliance is also an ongoing issue and HR leaders can no longer treat the security and privacy of employee data as the sole responsibility of IT. HR executives will play a key role in any company’s data breach response with new compliance mandates such as the European Union General Data Protection Regulation and the Australian Notifiable Data Breaches scheme apply to the protection of employee data.
HR leaders can expect more, not fewer privacy laws in the future.

Best Practices for Securing Sensitive Employee Data
To secure sensitive employee data, an organization must go beyond common security mechanisms like role-based access control and encrypted network connections.
Large enterprises often segment their HR systems and the IT staff that manages them, however this approach is increasingly ineffective as HR departments move to the Cloud, employees work from home, and HR users store more and more employee data on general use file servers and shared drives.
The best practices for securing sensitive employee data and ensuring compliance include ways of anticipating and preempting accidental and malicious ways sensitive employee data may be improperly disclosed, as well as putting controls in place to reduce to an acceptable level the impact of an employee data breach.
Know Every Location Where Sensitive Data is Stored
The first step in protecting and securing sensitive employee data is to realise employee data resides in far more places than just the Human Resources Information System (HRIS) and payroll solution.
Although HRIS environments are the main repository for payroll, benefits, and other administration, HR employees constantly export that data and store it in other places.
Email and email attachments are commonly used to exchange sensitive data with employees, other departments, and third-party service providers.
Use Multi-Factor Authentication
Outside attackers understand that the best way to compromise data is to compromise the account of someone that can access it.
MFA helps protect sensitive data by requiring that a user must successfully enter something they know (a password) and something they have (a numeric code texted to his or her mobile phone) in order to access this data.
Reputable providers of cloud HRIS systems will offer MFA as a feature, however legacy systems like a departmental file share, may or may not support MFA.
HR executives must demand that MFA is enabled, at least for remote and IT administrator access to systems that contain sensitive employee data.
Onboard and Offboard Employee Access to Sensitive Data
Part of onboarding and offboarding employees is ensuring they have access to the systems required to do their jobs when they join and then making sure that access is removed when they leave or are reassigned. The same must be true for access to sensitive employee data.
HR departments need to take responsibility for making sure access to sensitive employee data is properly managed. This does not mean you need to do the job of IT, but you do need to verify that IT is configuring access to employee data according to business need to know and corporate role-based access policies.
Ensure IT Administrators Cannot Expose Sensitive Data
Because IT administrators have full access to all data HR professionals you need to ensure IT administrators cannot mistakenly or maliciously expose sensitive data.
Most IT personnel are well-trained and trustworthy, but there are always those that cannot resist the temptation to know the salaries of other employees, who have a history of substance abuse, or access to the result of a privileged investigation.
Further, outside attackers often, if not always, compromise IT administrator accounts because they know those accounts have full access to all data.
Requiring MFA for IT administrator accounts will help but MFA does not change the fact that IT administrator accounts can be used by employees or attackers, mistakenly or with bad intent to access data they should not see.
The Cocoon Data Solution
Cocoon Data’s Cocoon Data will help control sensitive employee data that needs to be distributed to employees securely. Cocoon Data helps HR departments to not only decrease risk of an employee data breach and ensure privacy compliance, but allows HR to establish a multilayer access control to provide granular security depending on the sensitivity of the file.
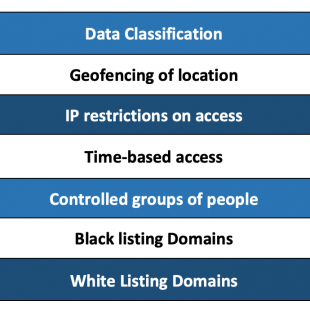
Documents and spreadsheets are easily classified in Cocoon Data. This allows secure distribution of files at the correct permission level, as set by the organization’s policies. Without the risk of someone inadvertently mistaking sending sensitive data like employee information to the wrong email address, of which can easily occur.
Cocoon Data helps to achieve greater efficiency and quality of HR processes because of improved data management.
Prevent Unauthorised Data Breaches
Data encryption is a basic risk management control that addresses some forms of unauthorised access and Cocoon Data solutions provide transparent and persistent encryption for all sensitive employee data.
Cocoon Data is unique in that encrypted data cannot be decrypted by IT administrator accounts. This approach means that IT administrators can continue to support the HR systems but neither they nor the attackers that compromise their accounts will be exposed to sensitive data.
Manage and Monitor Data With Centralised Role and Label-based Access Controls
Cocoon Data also include centralised role and label-based access controls to sensitive employee data, providing HR departments and IT an easier way to manage and monitor entitlements for data.
Role-based access control is effective for managing access to containers of sensitive employee data while label-based access controls work best for managing access using data classification (e.g. when a file share, for example, contains both sensitive and public data).
This ensures secure onboarding and offboarding employee access to sensitive data.
Protect Sensitive Data Distributed to External Users
Cocoon Data provides a secure Enterprise File Sync and Share (EFSS) solution so HR departments can distribute sensitive data to external users without compromising security or the ability to maintain control over information once it’s left the organization.
Files can be protected in a variety of ways including:
- Geofencing – protects your files by location or country
- Time Based Control – limits access to within a time period
- Dynamic Watermarking – discourages and records taking a screenshot
- Enabling/Disabling either files or users – important for compliance
And as more and more employees work remotely, Cocoon Data’s secure Enterprise File Sync and Share solution affords HR departments the protection of a VPN with the ease of use and accessibility of the Cloud.
Ensure Privacy Compliance and Monitor and Respond to Suspicious Behaviour
Cocoon Data includes a reporting capability to provide a history of access to secured employee data. This history easily integrates with existing reporting and monitoring solutions and allows organizations to not only monitor for suspicious behaviour, but also prove they have taken appropriate steps to maintain privacy of sensitive employee data. Both capabilities are critical to privacy compliance.
Maintaining a record of access to sensitive data also helps in less obvious ways. It is generally accepted that persistent (not necessarily sophisticated) attackers will eventually compromise an environment. However, with proper data security controls in place a security incident does not necessarily mean that there has been a breach of sensitive employee data.
When a security incident occurs, it is critical to quickly confirm whether sensitive employee data was improperly accessed. Having a detailed record of access to data helps determine if an attacker successfully exposed sensitive data. With that said, properly securing employee data will dramatically reduce the probability that an attack on sensitive employee data is successful.
A Data-Centric Secure Solution to Human Resources Data Privacy and Compliance
Due to increased employee expectations of privacy, increasing privacy regulations and more employees working remotely, Human Resources departments play an increasing role in the security of sensitive employee data.
But the good news is…you don’t have to become an IT expert yourself or rely on your IT department to protect your sensitive employee information and ensure privacy compliance.
Cocoon Data’s platform provides the full suite of data and security management capabilities required to reduce the risk of an employee data breach and improve the management of all workplace and employee data.


